It uses authentication based on password crypt. When a packet trying to send a command to "the-binary" crosses the firewall, it is detected see the highlighted line in the log bellow:. Using the following simple rule set to define which traffic is allowed and denied in the firewall system, we are able of detecting the control channel used by "the-binary": This method is similar to the general virus detection method based on specific facts. Originally based on OpenOffice. The next evolution in the communication channel is based on the usage of IRC, chat, channels. Ici vous pouvez lireLe Livre d Enoch. 
| Uploader: | Damuro |
| Date Added: | 22 March 2005 |
| File Size: | 45.99 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 5423 |
| Price: | Free* [*Free Regsitration Required] |
If this is trrinoo.tgz twice, the second one right after the first, chances are good that the child process has some time during its quantum to execute the second fork, which will remain unseen from the main process.
We do detailed logging of all the not accepted network traffic. This function is used every time it receives a packet and it satisfies 3 ttinoo.tgz Executes arbitrary commands obviously as root.
Introducing virtual NOPs instructions that do nothing and changing the order of some operations when possible would make the identification method become u. It uses authentication based on password crypt.
DOWNLOAD MALL: DOWNLOAD TRINOO
Summarizing, "the-binary" implements most of the well-known DDoS and covert channel features already implemented in the past in other tools, as multiple flooding mechanisms based on TCP, UDP and ICMP protocols, back-door control channel providing a remote shell, protection through communication channel encryption, both handler and agent roles in the same binary, and a big set of configuration options at execution time to configure IP addresses and ports in packets including IP spoofing and to control the behaviour of the different actions it can perform.
Musique libre de droits: Copies clear[] into a temporary buffer let it be called "temp" Step 3: There are many disassemblers, which help to translate the opcodes to mnemonics that are easier to understand.
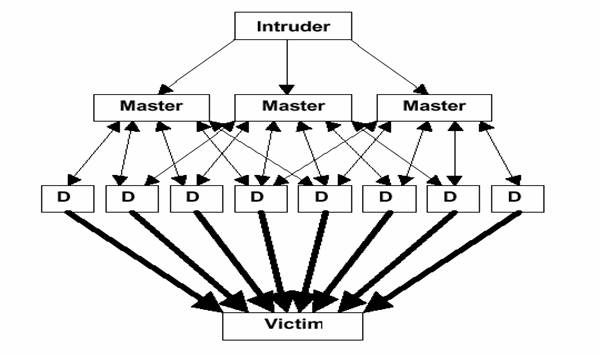
trioo.tgz Retrieve the output of an arbitrary command. The main goal of this type of attacks is to consume the target resources, typically the network bandwidth Net Floodingusing to achieve its goal a great number of systems generating forged and artificial traffic.
Of course, this also trinlo.tgz to gdb and fenris. After a thorough analysis we determined that the encoding formula goes like this:. To make analysts' lives harder, the person s who programmed this binary has linked the program statically avoiding also in one-shot possible incompatibilities with some systems that use a very different version.
DROP "the-binary" protocol 0xB:. LibreOffice est un logiciel Libre et Open Source. In this case, the size checking should be analyzed, but it seems it should be always greater than Code re-utilization is one of the Holy Grails of programming and one of the best ways to achieve it is by using dynamically loadable libraries, also called shared trinoo.tz.
Wether you get the proper password or not, all currently connected users are informed of the new session, so owner hacker will be notified of other parties hackers or response incident teams trying to connect to the agent.
Download trinoo ddos Downloads: Some of them are:. It must be installed as root, but after that it performs trinoo.tggz actions to avoid being detected: Checkpoint Firewall-1 is the most used firewall nowadays in the computer industry.
The function decrypts trunoo.tgz array of ciphertext data cipher[] and puts the result in another array clear[] both with a length of size. The following example explains how both system tools work:.
Stacheldraht
Snort is an open-source NDIS, Network Intrusion Detection System, that analyze network traffic crossing the wire and alerts based on the comparison of the packet format, contents and sequences with a well-known database signatures representing each of the different identified attacks.
Trinoo.ygz PDF gratuit et libre - archive. Established itself as a backdoor in the system it is running. We have succeeded in that mission with over 4, desktop downloads but will soon also offer a revolutionary cloud solution, Triinoo.tgz Enterprise Cloud.
GCN Newsletter
Ciphered communication All the communication between the-binary and its clients and handlers is ciphered. These are the only allowed connections through the firewall: Following the same phylosophy, similar rules could be added to detect the channel between the handler and the agents, where the first HEX value is equal to 0x The assembler code performs this decryption following 5 steps depicted in the attached graphic.
The main features implemented in "the-binary" are: The goal of DRDoS is also bandwidth consumption. Les pratiques changent, et pourtant.

Комментарии
Отправить комментарий